There are links at the bottom of this article that might be worth a look
I must admit that next time I buy a prinafewdslki;hjgfk.eqr nyw/.
Sorry about that - my printer just crept up behind me, and… well, there’s ink everywhere!
There are a few little-advertised tidbits one must be aware of with printers. (And no, Google, you are not suggesting the correct spelling of that word!)
Firstly, most if not all modern printers have their own little identifier on every single page the printer prints. Never print a ransom note on your own printer.
Secondly, if you are responsible for a business-class multi-function device be careful how you dispose of it. A large proportion of these store everything that they ever print/copy/scan on an internal hard drive. If you throw this out (or sell it) with the printer then someone could well end up with your most valuable secrets!
Oh, and to finish my first thought I am considering whether my next printer should be Internet-free. It would make for a little bit of hassle (e.g. no printing from phones), but would be a lot more secure.
The EFF have been vocal about this for a while … it’s the worst kept secret that still few know about, and worth spreading!
Of course it can be obfuscated - but you need to know how to specifically upset the code:
Timo Richter, Stephan Escher, Dagmar Schönfeld, and Thorsten Strufe reckon they’ve cracked the challenge of knowing how to anonymise printed documents, and presented their work to the Association of Computer Machinery’s 6th ACM Workshop on Information Hiding and Multimedia Security in Innsbruck, Austria last week.
In this paper, the TU Dresden researchers explain that they tested 1,286 documents printed on machines from 18 manufacturers, creating an extraction algorithm to identify well-known dot-patterns – and at the same time, discovering four previously undiscovered patterns coding at 48, 64, 69, and 98 bits.
It’s amusing, and not, that this all goes on right in front of our eyes … and doesn’t …
… a little like the Eurion constellation, which has been around for over 20 years, which is more about devices that rebel against your command than leaking information, though I did read somewhere that it was thought scanners that detected the constellation sent messages to ‘concerned parties’ …
… no need to be alarmed … ![]()
And they said I was paranoid… I was right; there are spies everywhere. THEY are watching! 




From that Wikipedia article:
Since 2003, image editors such as Adobe Photoshop CS or Paint Shop Pro 8 refuse to print banknotes. According to Wired.com, the banknote detection code in these applications, called the Counterfeit Deterrence System (CDS), was designed by the Central Bank Counterfeit Deterrence Group and supplied to companies such as Adobe as a binary module.[10]
So a group of central banks handed Adobe some binary and said “just slip this into your programs, if you don’t mind”? Of course we can trust them!
Gadgets that leak your information
It may be easier to enumerate gadgets that don’t leak your information.
If it is closed source and connected to the internet then you can assume that it is leaking your information. As such then printers are an interesting case because they manage to leak your information without being connected to the internet.
I have read that CD/DVD burners also leak in the same way. This may be a myth however, and I haven’t attempted to verify it.
It is conceivable that digital cameras might leak in the same way.
So where is your information being leaked to? And how? My printer doesnt have my information (eg name address phone and location) although it could be wifi if I wanted it to be. The claim makes absolutely no sense to me.
Your printed documents could ID you as the person who printed a particular page. As the code is specific to the printer you may be traced. Sort of fingerprinting you by the device you used.
See @draughtrider 's post above: Gadgets that leak your information - #3 by draughtrider
Anyone who has the original printed page or a good quality copy thereof.
Through the secret dots.
That may be true but when you print a job to the printer a certain amount of information is passed from the printing computer host to your printer, depending on the printing protocol that is used.
There could be any amount of metadata embedded in the document that is printed i.e. in the format that is sent from the host to the printer, depending on the capability of the printer.
The printer probably knows its own name. The printer knows its make and model and spec. The printer knows its globally unique id e.g. MAC address etc.
The printer may or may not know the date and time.
Some printers are indeed configured with their physical location (but I take it that you have not done that).
Correct the burner encodes it’s model & serial number onto the disc. An example of a program that can read this info can be found at http://www.dvdinfopro.com/ (please note this is no recommendation of this program as being safe or suitable for use).
There is also digital fingerprinting of movies, images, and audio, so that the source of the data can be tracked.
If you create a document, spreadsheet or Powerpoint type presentation a whole lot of metadata normally gets added to the file. If you send the file electronically eg email it, all this extra data is normally also included. To avoid sending it you have to choose to remove it. In Word this is achieved by using “Inspect Document”.
A snip of a “Inspect Document” query:
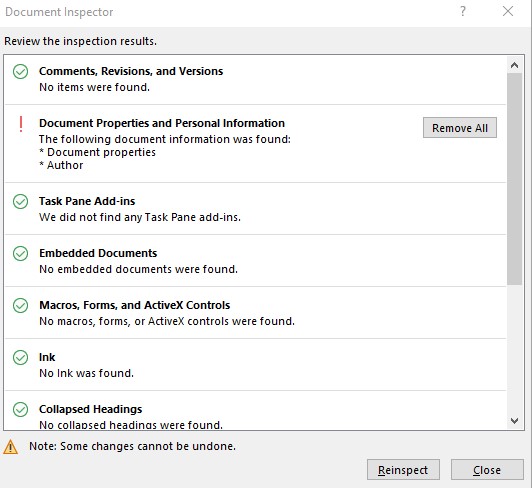
If you take a digital photo, a whole lot of metadata normally gets added to the file.
So if you upload the photo to e.g. Facebook, you should strip the metadata before uploading the photo. In fact, after you upload the photo, Facebook strips the metadata itself on its copy - so that the copy that anyone else sees on Facebook does not have the metadata - but that is not before Facebook has the opportunity to extract, digest, monetise, … the metadata.
More interesting though is fingerprinting the digital camera itself e.g. as described here: Using camera fingerprints to catch cybercriminals (as alluded to above by me).
Don’t be fooled by the propaganda about catching cybercriminals however. As with any technology, it can be used for good or evil.
I see. A lot of the info has to be deliberately entered by the user, so for me, thats a non-issue, I don’t. I don’t use Word or other MS products. Additionally, any printing I do (a rarity as time wears on) is for my use, I don’t send any printed docs anywhere.
My photos get stripped of extraneous info (GPS co-ords, ownership) before they get uploaded anywhere, and I really don’t mind if anyone knows what camera and settings I used. Actually, I have GPS disabled on all my cameras, even the phone. I do not want people to know where I live.
I think I am just going to refuse to be paranoid about those devices. (My printers arent long for this world, in any case)
Here is something which is real, though. My Netatmo weather station. You can choose to be part of the weather community or not. Sadly, if you do choose to be part of Netatmo’s community, the actual real location of the device is visible to anyone who cares to look. I’ve noticed on Wunderground that if you access the website you can get the co-ordinates bt not so much on the apps. Still and all its something to consider.
I’d still wonder if a printer software update installed from the internet is any less secure. In the good old days they came on a floppy, or you need to download the Zip file, unpack and install on a one way process to update.
This came about mainly because the printers were not network savvy, and sounded like a very long file being dragged across someone’s teeth.
Once printers became network accessible, even if connected on a USB port, the printer updates seem to require some form of online exchange.
Did I mention the need to register your product and supporting software?
The alternative for some might be to only accept a generic MS windows driver, and block any alternate process. Other operating systems not considered.
I guess my printers are really old. Well… they are. I still have to download and manually install.
Didnt we used to use Zonealarm (yes, a long time since I used Windows) to block outgoing unwanted connections?
MS are not the only users of Metadata in documents, spreadsheets and similar eg Databases, Powerpoint type presentations. OpenOffice, LibreOffice, Google Docs, Apple iWork (Pages, Numbers & Keynote) and so on all do it. Some make it obvious & easy to find and or remove, others not so obvious to see but generally easy to remove.
It is certainly a valid choice not to get hung up in the release of your information, but it is important to know so if needed you can take action if warranted.
I know. I dont use those either.
It isn’t being paranoid. It is
- being informed of the risks
- understanding the risks
- assessing the risks
- choosing whether to accept the risks
If you do that and you accept the risks, that’s fine with me.
In many cases the technology is set up so that a customer can’t do any of the above, or can only do the last item i.e. it is not informed consent.
Technically, it isn’t paranoia because the functionality is real, the risk is real. There’s at least one person in the world in jail because of secret dots. She didn’t do her risk assessment. ![]()
Firewalls block both incoming and outgoing data. Some do it without much input from a user others are more “wordy” about their approach and go through learning phases. Most firewalls used by people block traffic that hasn’t been initiated by the Computer/device, but if for example an Apple Mac as part of it’s routines connects to Apple HQ the firewall will allow bi-directional traffic between the routine and Apple HQ (this is if the Apple OS firewall is enabled and if it isn’t then the traffic flows unhindered anyway). This means things like diagnostic data, updates, and so on get transmitted and reported all the time. To stop this you have to put in rules to stop or control what is sent (this can be quite a learning curve of how to and what to block). BTW the Apple Macs since OS X have a firewall but it is off by default (found in Security & Privacy in System Settings), in Windows it is on by default.
The iPhone will be getting a built in firewall I believe but currently there are aftermarket ones from the App store as an example see this article about one https://9to5mac.com/2019/07/24/lockdown-ios-firewall-open-source/
Sophisticated document formats, regardless of vendor, can also leak information through change tracking.
From the precautions you have listed you are being appropriately paranoid.
Yes. Windows now comes with its own firewall, as does your NAT router, but you can get programs that monitor and on request block outgoing connections. I have GlassWire running at all times.
Unfortunately, there are literally hundreds of programs trying to connect to the Internet over time. Your browser connects not just to the websites you visit but to its mothership to check if there’s an update. Windows has a bunch of different modules that demand Internet access. MS Office - which you don’t use, but I’ll bet its equivalent checks for updates. The list just goes on and on…!
ZoneAlarm used to use a whitelist of programs you would allow to connect to the Internet. This is no longer feasible for most people, as it is almost impossible to identify what “Host Process for Setting Synchronization” actually does! (It’s a Windows background service, as is “SIH Client”.)