… has its very own topic: Medibank data breach
… and an update today:
Summary: bad guys got customer data but don’t worry because it’s safely encrypted …
Ahem …
It is very concerning. One hopes that their encryption is as good as they think it is.
The other enormous problem is it will result in phishing attempts to obtain the key/passwords. This is something that any Lastpass user needs to watch out for.
All Lastpass users should access their vault ASAP and systematically reset all their passwords on every stored login. This will then render the login passwords in the vault useless should they somehow be accessed in the future by criminals. It however doesn’t prevent them knowing user ids and other key login information where it may exist. One would need to monitor their accounts which were stored in Lastpass for any unauthorised access.
I would also seriously be thinking of using a different password manager.
It has been written up extensively, and audited.
While I am not a LastPass customer, I would not be particularly bothered by this. At most I would change my primary password.
Having heard a lot more about the LastPass breach and how the company stores data, I think it is now time to suggest moving to another password manager. While the following ‘Toot’ overstates some of the risks, it suggests that LastPass has not kept up with modern technology.
The following blog entry provides LastPass users with information about which parts of their user data are (or are not) encrypted.
And someone has put together a Windows PowerShell script to de-obfuscate data in your LastPass vault that isn’t encrypted but is obfuscated. Using ChatGPT to help (scary).
You can find guidance on using it here.
Small by the standards set by Optus and Medibank but: QUT confirms personal data of thousands of staff compromised in cyber attack - ABC News
An update from QUT. Original breach now understood to be several times larger than previously thought: More than 11,000 employees, students and former staff affected by cyber attack, QUT says - ABC News
This, received today …
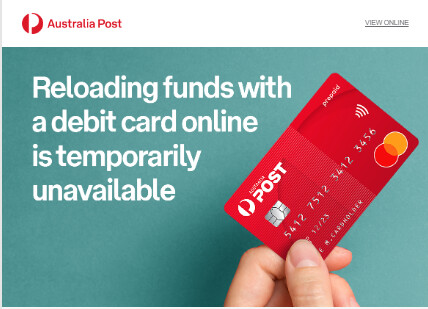
and …
… one wonders what the back-story is … it seems likely there was an issue, if so …
Australia Post has a Mastercard?! Does that mean any debt issued against it is government-backed?
Oh wait - I see from the website that someone has already thought of that and it’s only prepaid. And the website says nothing about this ‘temporary’ problem.
Today The Good Guys: The Good Guys customers possibly affected by data breach at former third-party provider My Rewards - ABC News
The latest security bulletin can be found at
It still states user data in the vault is safe as long as the Master Password has not been compromised by the user or is a re-used or simple password that can be copied or brute force attacked “And without the encryption key, no one, including LastPass or bad actors, has access to unencrypted data in a user’s vault”. This obviously is the same for any password we may use, if they are compromised, too simple or are used on multiple sites they are at greater risk of being found and used by bad actors. The data in the vault is encrypted and can’t be accessed without the password.
Among the security recommendations such as changing the Master Password if it has been a reused or too simple one (mine is somewhere far North of the recommended starting 12 character length), they also recommend that 2FA (Two factor authentication) be enabled and that the hashing iterations of the encryption key which uses the email address and password for generation, be increased to at least 600,000 iterations in line with the January 2023 released advice by OWASP which updated their recommended number of PBKDF2 iterations to 600,000. Lastpass are increasing the iteration default for all new Lastpass accounts to 600,000 but old accounts will need to check and update if needed.
Has anyone timed how long 600,000 iterations takes? I mean just roughly what sort of delay this introduces for the user?
(To put that number of iterations into perspective, your WiFi passphrase uses 4096 iterations - but WiFi had to be usable on relatively under-powered WiFi client devices, including devices of yesteryear.)
I kind of feel that if you need 600,000 iterations in order for it to be resistant to brute-forcing then you probably need to change the algorithm itself.
What was the previous default number of iterations for a new account?
PBKDF2 as an algorithm is actually parameterised with the HMAC which in turn is parameterised with the underlying hashing algorithm used. Hence PBKDF2 can be beefed up by using a ‘better’ hashing algorithm, without necessarily changing the number of iterations. However I think general security advice is that there are more robust overarching algorithms around than PBKDF2, and even that using a general purpose hashing algorithm for this purpose is not ideal.
(Hence it isn’t actually very meaningful to recommend “600,000 iterations” without specifying which HMAC is in use.)
Generally though: more iterations is better - to the limits of the delay that you are prepared to tolerate.
And a strong password is even better still (but still to be used in conjunction with an appropriate number of iterations).
Indeed.
Yes timed at 30 seconds to do so on my Intel Gen 11 i7 for the complete redo of the iterations, in fact mine was more than 1,000,00 iterations. It does state in the process it could take 3 to 5 minutes to carry out the task. After the re-iteration, a normal login to the vault takes about 3-5 seconds. Use it or don’t, however the advice still shows that the Vault is secure if the Master Password is still uncomprimised and of sufficient complexity…
They use the PBKDF2 function implemented with SHA-256, this may or may not use HMAC. Based on the number of iterations recommended with the function and using SHA-256 it is very likely HMAC is being used. The function used in hashing is a recommended method according to NIST and so while there are different ways, this is a proper method to carry out the hashing.
If you wish to delve further into the outside organisations advices regarding PBKDF2, which is a bit more technical than most users need to know, I am providing some information from OWASP and NIST. Further technical discussion of which is best is going outside the topic direction. If others wish to discuss the various ways and pros and cons of hashing please create a topic for that purpose.
OWASP notes that 600,000 iterations is the base number recommended for PBKDF2-HMAC-SHA256 and that the US National Institute of Standards and Technology (NIST) state PBKDF2 is a recommended method. At NIST they make note that PBKDF2 is a suitable method.
"
PBKDF2¶
PBKDF2 is recommended by NIST and has FIPS-140 validated implementations. So, it should be the preferred algorithm when these are required.
PBKDF2 requires that you select an internal hashing algorithm such as an HMAC or a variety of other hashing algorithms. HMAC-SHA-256 is widely supported and is recommended by NIST.
The work factor for PBKDF2 is implemented through an iteration count, which should set differently based on the internal hashing algorithm used.
- PBKDF2-HMAC-SHA1: 1,300,000 iterations
- PBKDF2-HMAC-SHA256: 600,000 iterations
- PBKDF2-HMAC-SHA512: 210,000 iterations"
From NIST on the suitability of PBDKF2 from 1 March 2023
"Verifiers SHALL store memorized secrets in a form that is resistant to offline attacks. Memorized secrets SHALL be salted and hashed using a suitable one-way key derivation function. Key derivation functions take a password, a salt, and a cost factor as inputs then generate a password hash. Their purpose is to make each password guessing trial by an attacker who has obtained a password hash file expensive and therefore the cost of a guessing attack high or prohibitive. Examples of suitable key derivation functions include Password-based Key Derivation Function 2 (PBKDF2) [SP 800-132] and Balloon [BALLOON]. A memory-hard function SHOULD be used because it increases the cost of an attack. The key derivation function SHALL use an approved one-way function such as Keyed Hash Message Authentication Code (HMAC) [FIPS 198-1], any approved hash function in SP 800-107, Secure Hash Algorithm 3 (SHA-3) [FIPS 202], CMAC [SP 800-38B] or Keccak Message Authentication Code (KMAC), Customizable SHAKE (cSHAKE), or ParallelHash [SP 800-185]. The chosen output length of the key derivation function SHOULD be the same as the length of the underlying one-way function output.
The salt SHALL be at least 32 bits in length and be chosen arbitrarily so as to minimize salt value collisions among stored hashes. Both the salt value and the resulting hash SHALL be stored for each subscriber using a memorized secret authenticator.
For PBKDF2, the cost factor is an iteration count: the more times the PBKDF2 function is iterated, the longer it takes to compute the password hash. Therefore, the iteration count SHOULD be as large as verification server performance will allow, typically at least 10,000 iterations."
So to summarise my comment about number of iterations …
- when you use a high number of iterations, you delay the hacker but you also delay yourself
- when you use a strong password, you delay the hacker without delaying yourself (well, apart from the typing that you have to do
 )
)
So I know which one I prefer.
And you can see how WiFi can be made as “secure” with only 4096 iterations as something else that uses 600,000 iterations. You can compensate for the fewer iterations by having one or two extra printable ASCII characters in your passphrase (all other things being equal).
Another kind of data breach: ANZ bank apologises after customers' personal information found in Perth skip bin - ABC News
![]()
Yeah that was poor.That’s what banks are like now we don’t care about our customers soon we will be closing our doors,and making more profit
And today’s: Latitude Financial hit by cyber attack, more than 300,000 identity documents stolen - ABC News
NB: If you have bought under finance from
major Australian retailers, including Harvey Norman, JB Hi-Fi, David Jones and The Good Guys
then this could be you.
This looks to be worse than Optus because the breach appears to involve full identity documents i.e. drivers licence including both licence number and card number. So this blows apart anything using the drivers licence for authentication where the authentication is checked by the government (banking, telco).
This is the initial media/ASX advice…
At this stage it appears that the personal information was that held by two other service providers. What the service provider relationship with LFS is, where the data was held or what customers have been affected is currently unknown.
It might be time for the government to mandate the use of its ID Matching for those organisations are prescribed by law to carry out ID document verification. Organisations keeping copies of verified documents on their servers makes them attractive targets for criminals/hackers. Mandating use of ID match could include provisions that organisations are no longer able to keep copies of personal document/records. Business which are also required to carry out identifying document checking should also be looking at using ID match even if the government fails to mandate its use.
And this is part of the bigger picture problem. Data is very slippery.
However, as discussed in this forum before, this would consequently require the government to provide a verifiable, unforgeable success indication back to the organisation that cannot later on be repudiated. If nothing else, this allows the organisation to be audited later on by the government itself that the organisation is following correct procedures for identification and verification by government.
Does the government’s existing interface for verification support that? No idea.
I must already do this as it is used by some financial institutions and other organisations/government agencies. If this wasn’t occurring, these organisations/government agencies would also be stockpiling a copy just in case. Our experience with the system is that second party collation of the data doesn’t occur and the verification occurs in a popup ID Match interface which then communicates the verification with the underlying institution.
The IDMatch website states:
Most organisations using the Identity Matching Services won’t need to keep copies of your identity documents, which helps to protect your privacy.
and
The Identity Matching Services use what we call hubs, which are technical systems that act as ‘routers’ to securely transmit matching requests between the organisation which is using the service and the agency which holds your information used on your identity document.
These hubs do not store or retain your identity information. They only retain transactional data for a limited period for auditing purposes.
It appears that the organisations keep transactional data, not identity information for records.