#Need to Know…?
thank you person for the correction! 
A reminder to be careful with texts. You never know where they’ve been.
https://www.washingtonpost.com/technology/2019/11/07/forgot-you-not-valentines-day-ghost-texts-arrive-months-late/
This is the US. Whether the situation in Australia is any less insecure, I don’t know.
iOS devices by default use ‘iMessage’ when communicating with each other. These are encrypted. Android is in the process of launching a similar feature. Unfortunately this doesn’t help people with one OS messaging the other (unless you use a 3rd party app)
Which is replacing SMS with RCS messaging next year. Unfortunately, that does not appear to mean faster or more secure messaging. (Apparently Telstra calls it Telstra Messaging.)
Or more reliable. It’s still a “best effort” service. There’s no guarantee how long delivery will take - or even whether the message will be delivered at all.
A few years back, a mate recounted a presentation he gave to a group of managers. The managers had developed a habit of communicating by SMS. He was there to tell them that SMS isn’t terribly reliable. While he stood before them, his 'phone sounded. It was an SMS that one of the managers had sent him the previous day. At least it eventually turned up. ![]()
Not quite 2020 news but getting close is that Wyse lost control of about 2.4 million customers/users data including email addresses, tokens used for Alexa, due to what they say is an employee mistake. To read about the issue the link following has more about it:
‘Human error’ describes what happens when you haven’t adequately trained your employees and/or you have system design that inadequately considers the human element. In other words, it is a cop-out.
Topping off this week’s Wyze hack warning we also have the Amazon Ring Video devices being hacked which has been an ongoing problem not yet fixed but being litigated:
https://drillwarrior.com/can-a-ring-video-doorbell-be-hacked/
A bit of a worry:
You can argue that in general. Some cases it is manifestly true that training was inadequate. Some cases it is arguable that the design was not sufficiently failsafe to be used by humans. However in this particular case they do give us:
An employee working on the project mistakenly removed this security, exposing the data.
Sounds like an IT department error in a development / testing environment - so I don’t think either of the above completely fits.
My question would be: Why does a development / testing environment have to be accessible from the internet (my assumption) at all?
But the bigger question would be: Why do companies keep on designing products that can even be subject to these issues? (Rhetorical question, I know the answers.)
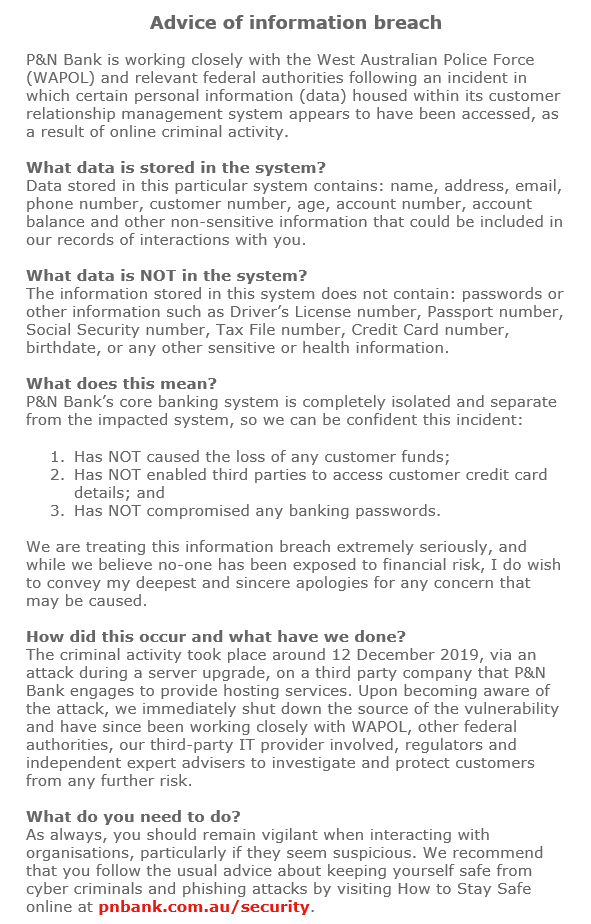
They seem to think that you should feel relaxed and comfortable that your money hasn’t all been stolen, while failing to notify you of the risks associated with this breach. Given that the miscreant(s) now have your email address, name, phone number, age, and a bunch of other information about you a spear (targeted) phishing campaign is quite likely. Additionally, you can probably expect to start receiving more spam than you have in the past, once the hacker(s) has/have got all they want out of the data and see more value in on-selling the list.
Although P&N is member owned, I agree that doesn’t excuse not including resources about phishing. I’ll certainly remember this at the next board meeting…
Provided that it is a genuine email, and not itself spear phishing.
That would be the first question I would ask: Without clicking on any link in the email, can I verify via another mechanism that this is genuine?
Fortunately this one seems legit: Alerts & Notifications | Help & Support | P&N Bank
Why would someone use this english to describe personal information? “Data stored in this particular system contains; name, address, email, phone number, customer number, age, account number, account balance and other non-sensitive information that could be included in our records of interactions with customers” What included information was non sensitive? From the way it is stated your address, name, email, age, account number, and customer number. I personally think that is very sensitive information, doesn’t the Bank? Perhaps it would have been better to have written “and some other information that was non sensitive data from our records of interactions with our customers”.
It strikes me that perhaps as a member owned institution they simply didn’t have these sort of contingency plans in place. These sort of documents should be pre written by a team of lawyers in preparation for inevitable incidents. In this age as a business you should act like a breach will happen and make sure you’re prepared.
I think you have deciphered it. I think what they are trying to say is that there is other information and that other information is not sensitive, so they haven’t itemised it.
Perhaps by ‘sensitive information’ they mean ‘personally identifying information’ (PII) or ‘personal information’. What is personal information? | OAIC
I would cut them some slack. Maybe the alert was put together in a hurry, without time for expert proof-reading.
I think that’s a bigger issue than the breach itself. That there wasn’t already a plan developed by experts in place.